Triage once again proved invaluable in collecting statistics on malware exhibiting evasive behavior against static analysis. While preparing for my talk at BSides Athens, I wanted to assess current trends in this category—and figured it would be a missed opportunity not to extract additional insights from the dataset. Since it's also been a while since my last blog post, this seemed like the perfect moment to put the data to good use. And so, this post was born.
Lets get started first with some general information:
Total apps scanned: 114674
Apps with valid permission lists: 93515
Average number of permissions per app: 24.84
Average number of services: 7.29
Average number of broadcast receivers: 5.63
Average number of activities: 27.27
Percentage of apps with JobScheduler or background-like services: 27.78%The following figure shows the top 10 most requested permissions and as expected the "Internet" permission is the most requested one.
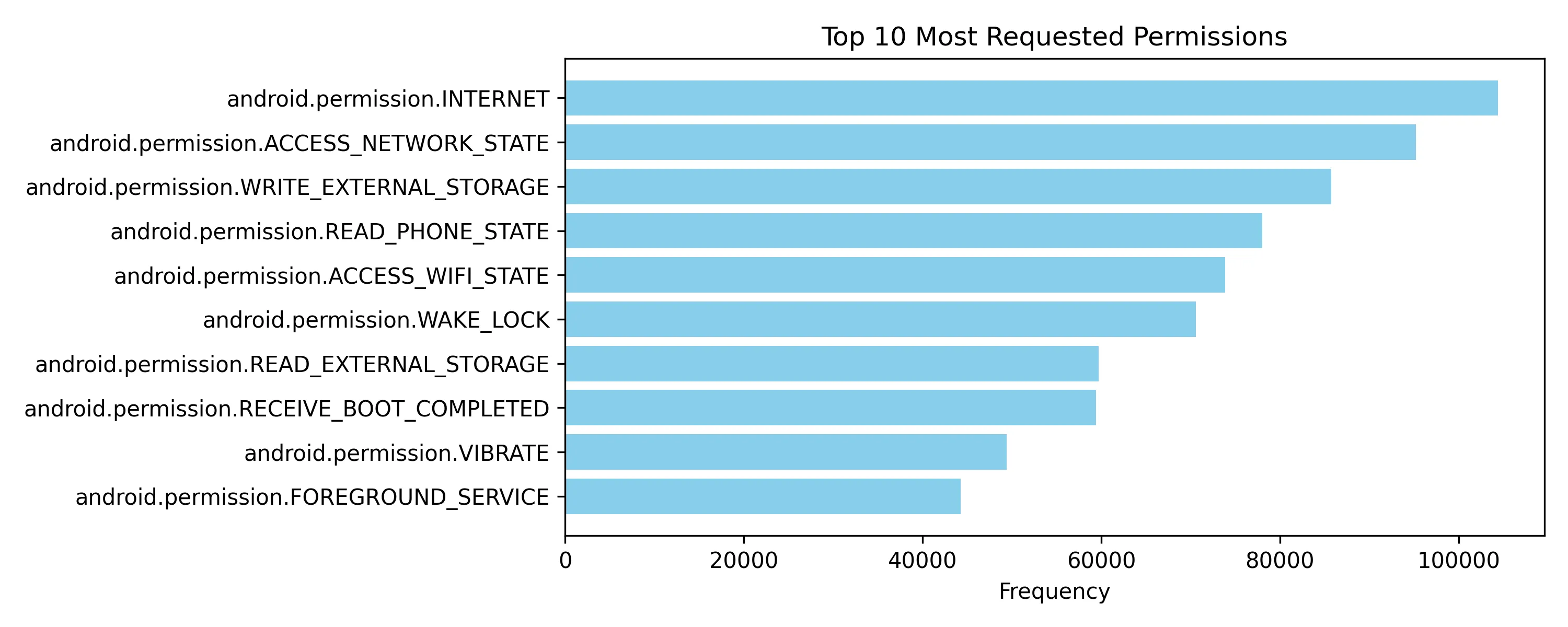
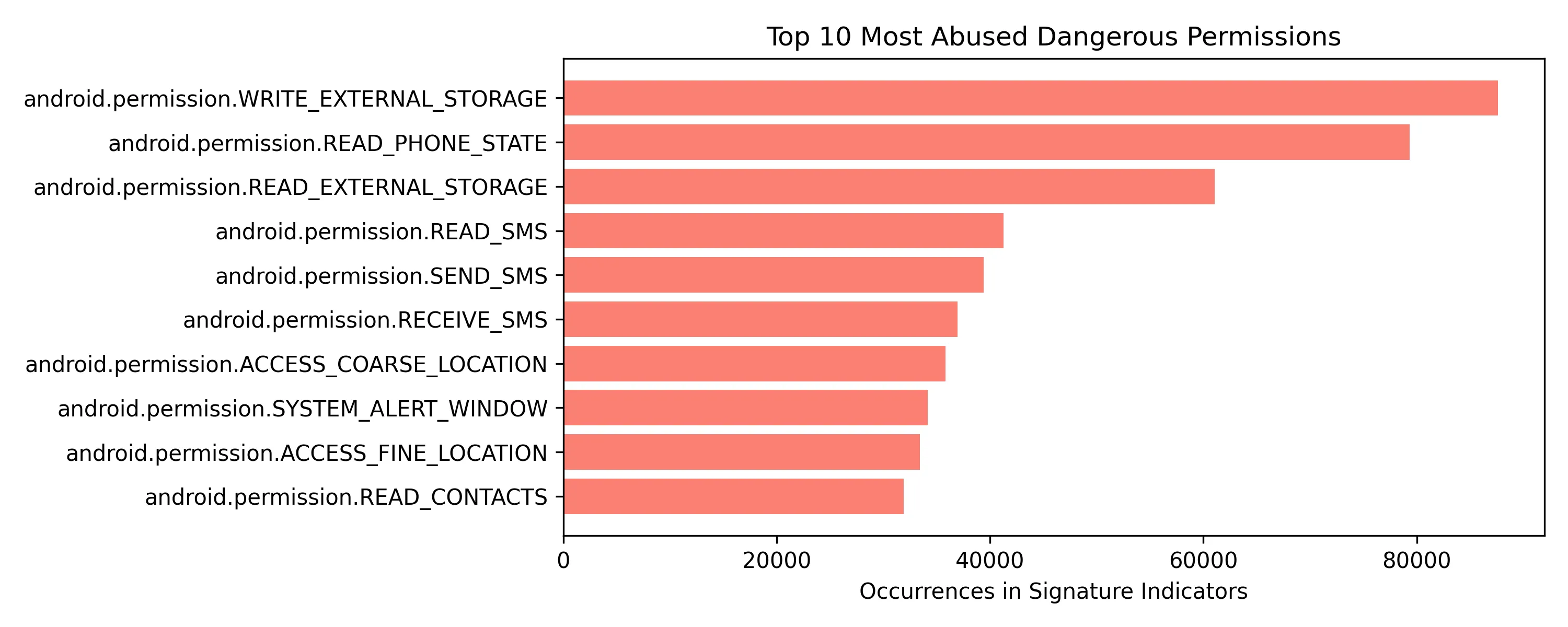
What about the top 10 most abused dangerous permissions?
Continuing, one of the most telling indicators of malicious behavior came from broadcast receivers: over 1,800 apps included an identical SmsReceiver class, while 1,200+ others used near-identical obfuscated receiver names like com.nameown12.p060d. These receivers are configured to listen for SMS_RECEIVED and WAP_PUSH_DELIVER broadcasts — a known tactic in spyware and banking trojans. The scale and repetition of these classes across unrelated apps strongly suggest a coordinated malware campaign or shared dropper framework.
Top receivers listening for SMS/WAP intents:
com.example.application.core.telephony.sms.SmsReceiver: 1814
com.example.application.core.telephony.sms.DeliverySmsReceiver: 1814
com.nameown12.p082q: 1295
com.nameown12.p079x: 1295
com.nameown12.p042g: 1295
com.nameown12.p060d: 1295
ru.cvv.core.SMSBroadcastReceiver: 1002
com.example.application.core.WapPushReceiver: 907
net.dinglisch.android.taskerm.ReceiverStaticInternal: 881
cmf0.c3b5bm90zq.patch.C10: 849Next, this metric highlights frequently reused classes across all analyzed APKs that do not belong to Android's core framework. These are typically Activities, Services, or Broadcast Receivers from third-party SDKs (like ad networks, location providers, payment gateways) or injected by developers and their high reuse can indicate:
- Bundled SDKs like Alipay, Unity Ads, or JPush, found in thousands of unrelated apps.
- Repackaging or trojanization, where common components are cloned across fake or malicious apps.
- Shared malware toolkits or APK generation kits reusing the same class names.
By identifying which classes appear most often, we get a clearer picture of what SDKs, behaviors, or obfuscation patterns are being reused at scale. This is particularly useful for attributing malware families and detecting mass-produced droppers.
Top reused **non-framework** component class names across all apps:
com.alipay.sdk.app.H5PayActivity: 7262
com.tencent.tauth.AuthActivity: 6833
com.tencent.connect.common.AssistActivity: 6832
cn.jpush.android.service.AlarmReceiver: 4369
cn.jpush.android.service.PushService: 4366
cn.jpush.android.service.PushReceiver: 4365
cn.jpush.android.ui.PushActivity: 4319
com.unity3d.services.ads.adunit.AdUnitActivity: 3813
com.unity3d.services.ads.adunit.AdUnitSoftwareActivity: 3803
com.unity3d.services.ads.adunit.AdUnitTransparentActivity: 3801
com.unity3d.services.ads.adunit.AdUnitTransparentSoftwareActivity: 3801
com.baidu.location.f: 3694
com.alipay.sdk.auth.AuthActivity: 3600
cn.jpush.android.service.DaemonService: 3533
cn.jpush.android.ui.PopWinActivity: 3116
com.applovin.sdk.AppLovinWebViewActivity: 2969
org.eclipse.paho.android.service.MqttService: 2947
com.applovin.adview.AppLovinFullscreenActivity: 2860
com.applovin.mediation.MaxDebuggerActivity: 2752
com.applovin.impl.adview.activity.FullscreenAdService: 2742Next an analysis on the Java package namespaces (like com.tencent, com.applovin, com.nameown12) used in the apps was done. These prefixes indicate the logical ownership or branding of the codebase and are a powerful tool for spotting:
- Legitimate popular apps or SDKs (
com.spotify,com.whatsapp,com.bytedance) - Suspicious or synthetic namespaces (
com.nameown12,com.example) often used by malware to appear generic or avoid detection - High-volume fake apps, clone networks, or grayware distributions using the same namespace across thousands of variants
This analysis gives insight into which developer identities dominate the app set — and can highlight coordinated campaigns or shared malware families through their naming patterns.
Top reused **non-framework** package prefixes:
com.spotify: 163086
com.whatsapp: 97464
com.tencent: 84223
com.nameown12: 66141
com.qihoo: 59906
com.morgoo: 52366
com.ss: 48474
com.bytedance: 47144
com.applovin: 45380
com.instagram: 44249
com.gbwhatsapp: 40637
com.baidu: 36869
com.vega: 32145
com.xgbuy: 31063
cn.jpush: 29112
com.umeng: 28045
com.mobile: 27740
com.example: 26134
com.snaptube: 25605
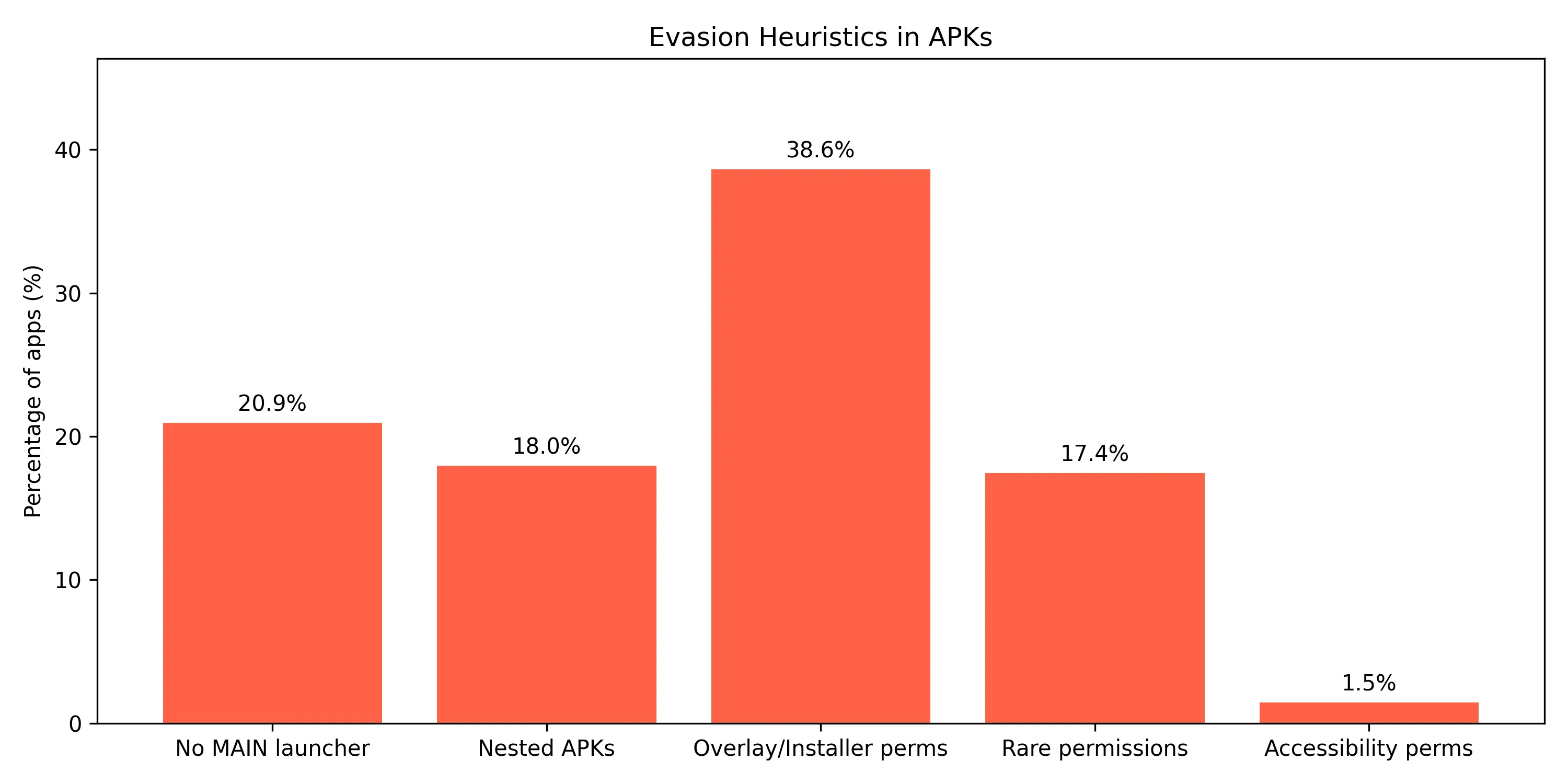
com.roblox: 22939Another interesting thing to see is evasion heuristics being used:
Another interesting statistic to see is the distribution of the static analysis scores assigned by Triage:
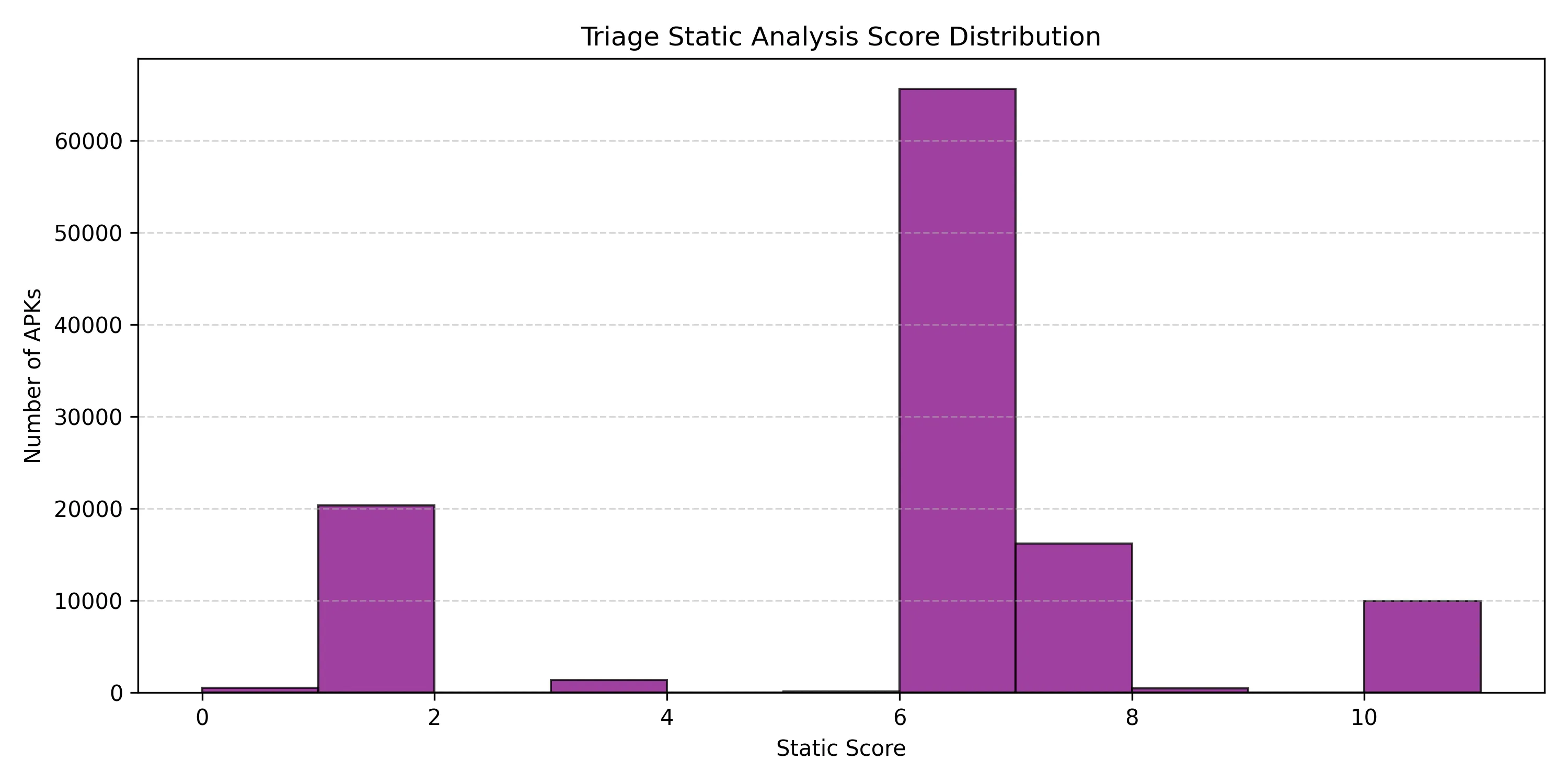
Complementary to that lets also see the signatures for all APKs with score higher than 5:
Top signatures in high-score apps:
Requests dangerous framework permissions: 90788
Declares services with permission to bind to the system: 20535
Attempts to obfuscate APK file format: 10621
Declares broadcast receivers with permission to handle system events: 10360
Android SoumniBot payload: 2666
Soumnibot family: 2666
Spynote family: 1821
Irata family: 1265
Spynote payload: 1209
Irata payload: 962
Octo family: 864
Octo payload: 860
UPX packed file: 620
Unsigned PE: 543
Patched UPX-packed file: 459
Ermac family: 432
Ermac2 payload: 432
Ajina family: 295
Android Triada payload: 212
Triada family: 212Do note the Attempts to obfuscate APK file format that indicates some kind of tampering either in the ZIP structure on the AXML part.
Finally the plots below should offer a useful starting point for exploring the relationship between an APK’s size and its internal complexity. By mapping size against the number of declared permissions, services, receivers, and its static analysis score, we can begin to distinguish between legitimate complexity (e.g. feature-rich or SDK-heavy apps) and suspicious bloat (e.g. obfuscation layers, embedded payloads). However, interpreting these patterns in isolation can be misleading. To make meaningful inferences, such as identifying outliers that are likely malicious, we would need to compare this data against a well-defined set of benign, known-good applications (e.g. from playstore). This would help determine whether certain correlations (like high service count in large apps or dense permission use in small ones) are genuinely abnormal, or simply reflective of normal app diversity.
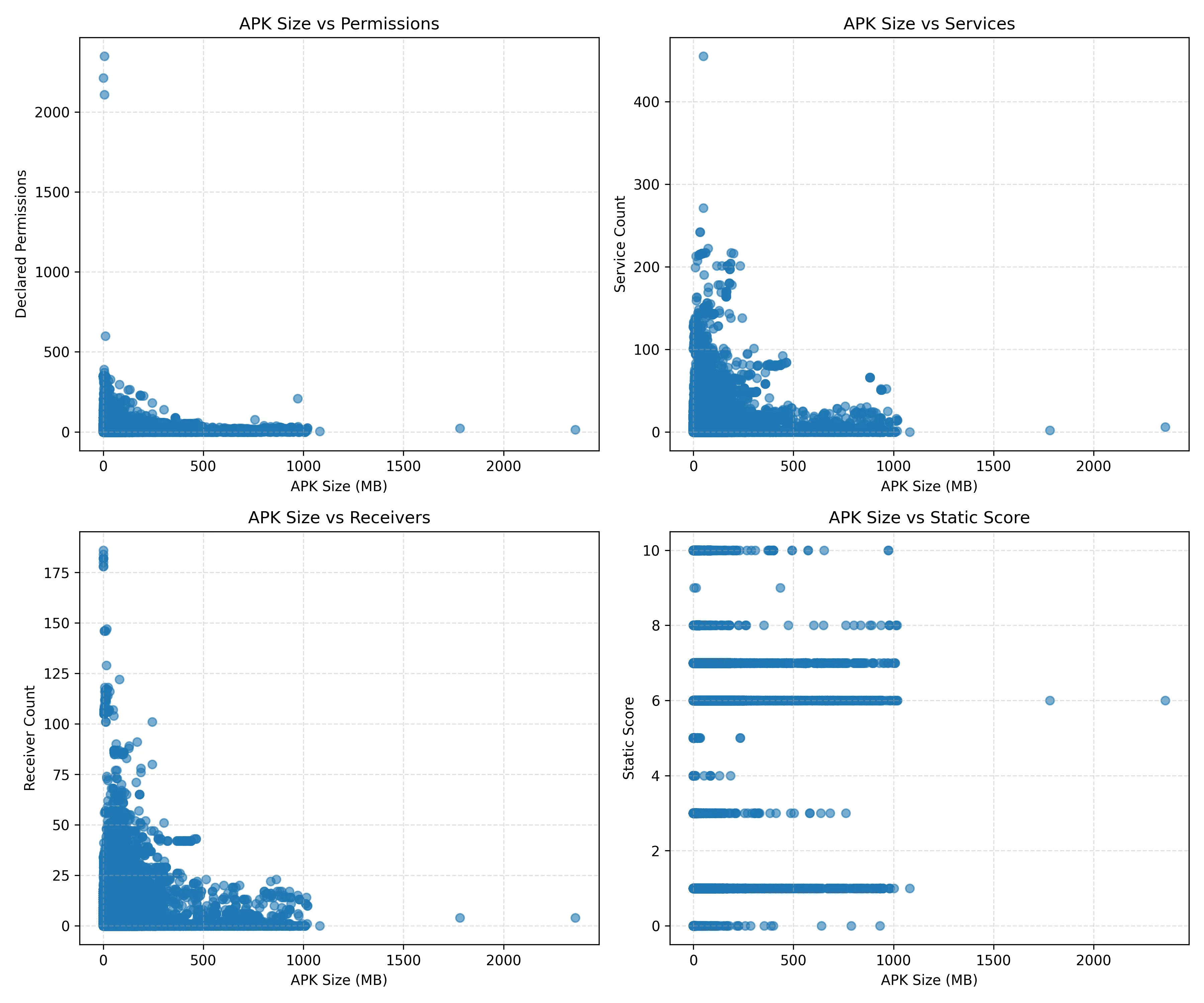
I hope these statistics sparked some interest! Please feel free to reach out to me if you have any ideas or questions. Enjoy!