I am thrilled to share that my research on static analysis evasion techniques in Android malware, which began in August 2023, has reached a significant milestone. This research has matured to a level where It could be shared with Google, and guess what? 🎉 Google has acknowledged the validity of our findings and rewarded all the effort and time put into it! 🏆
The figure below shows the email received by Google.
Moreover, together with my friend and colleague Kaloyan Velikov, who helped finalize this research, we will be presenting it at 🎤 Defcon! 🎤
The purpose of this post is not only to share this exciting news but also to provide a brief and condensed review of the research. Consider this a sneak peek of our upcoming presentation at Defcon Demolabs.
Rising Threat of Evasion Techniques
The data for the analysis presented in the following figure was obtained from tria.ge, which is a state-of-the–art malware analysis sandbox. They where kind enough to provide me with researcher access, which I used to identify Android applications that exhibited signs of employing evasive techniques.
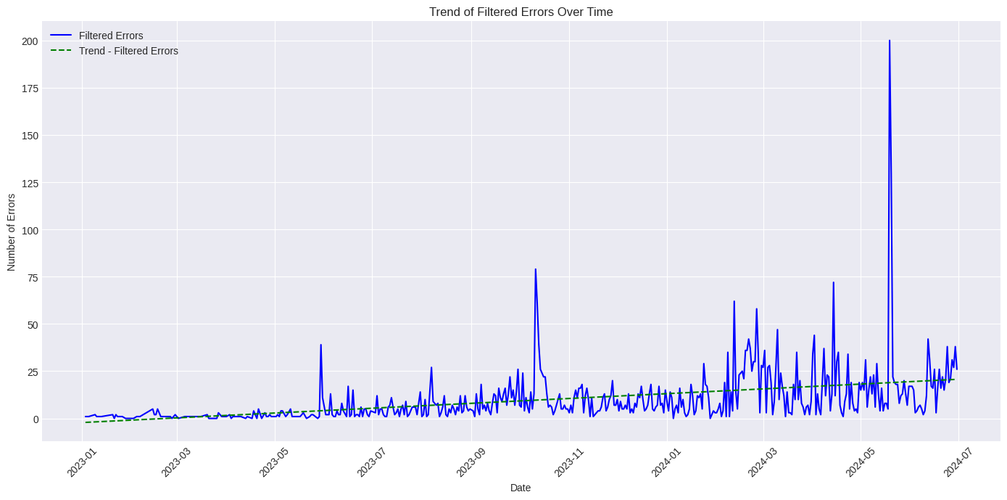
It is evident from the data that there is an upward trend in the number of evasive APKs being uploaded to tria.ge for malware analysis. It is highly likely that services offering static analysis evasion methods have already been developed, contributing directly to the observed upward trend. It’s a clear call to action for the cybersecurity community to adapt and evolve alongside these emerging threats.
What Are Evasion Techniques?
Evasion techniques are methods used by malware to avoid detection by static analysis tools. The full list of evasion techniques covered during our research is the following
- End of Central Directory record defined multiple times
- Unknown compression methods
- Compressed entry with empty filename
- Unexpected starting signature of AndroidManifest.xml
- Tampered StringCount value
- Strings surpassing maximum length
- Invalid data between elements
- Unexpected attribute size
- Unexpected attribute names or values
- Zero size header for namespace end nodes
While we won't dive into the specifics of each evasion technique in this blog post, it is clear that these methods target either the ZIP structure of the APK or the structure of the AndroidManifest.xml file.
For a more comprehensive analysis, we will release a detailed white paper based on this research in the coming months. If you don't want to wait, we would be more than happy to see you live at our Defcon Demolab presentation.
Existing Tools Falling Short
Despite the progress in malware detection, many existing tools still fall short when it comes to identifying sophisticated evasion techniques. We have already seen in a previous post that tools like Jadx, Apktool, ApkAnalyzer, and Androguard are effective for general analysis but often struggle with advanced tactics used by modern malware. These tools can miss critical manipulations within the ZIP structure of the APK or the AndroidManifest.xml file, allowing malicious apps to bypass security measures and pose significant threats to users. This gap highlights the urgent need for more specialized tools to combat the evolving landscape of Android malware.
Introducing apkInspector
apkInspector was born out of this research, a tool designed to detect and bypass static analysis evasion techniques in Android malware. This tool marks a significant advancement in our ability to combat these threats. While apkInspector will continue to evolve to counteract new malware strategies, it is already stable and robust. We are proud to announce that apkInspector is now integrated into two major open-source projects, providing the community with the necessary tool to identify and mitigate evasive malware.
Why Should You Care?
From a normal user's perspective, you will benefit from increased protection as malware employing such techniques will be more easily detected, and you will receive alerts more quickly. For developers and researchers in the Android ecosystem, this effort aims to shed some light onto these evasive methods and encourage the open-source community to adapt and respond to them effectively.
Join us to our Defcon Demolab presentation in Las Vegas! https://forum.defcon.org/node/249604