In a similar fashion like the article about cracking a shadow file with John, we thought it would be a good idea to include how to crack SSH keys using John. It is another common concept you see in CTF events but also in real life. The process is relatively simple and the cracking method to chose is up to you. In this tutorial we are going to bruteforce the password using one of the common wordlists available in Kali.
First thing is to prepare the key so it will be in a format John understands. For this purpose we have the ssh2john.py tool. In order to find it in you system you can use locate or if you want to download it, you can find it here.
Now lets imaging the ssh key we need to crack is named protected_key. We convert it so john can crack it by executing
python ssh2john.py protected_key > protected_key_john.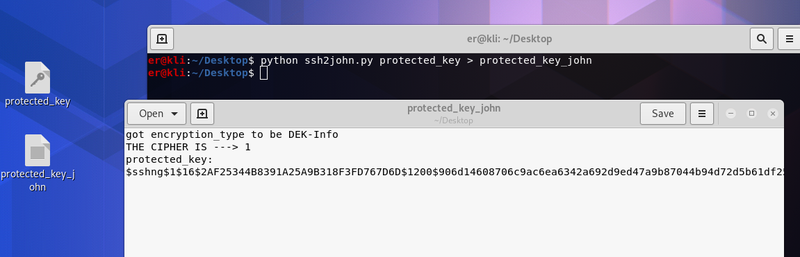
We now have a format John can understand and crack. We can see in the picture above the contents of the protected_key_john.
Final step is the actual cracking, we simply find a wordlist of our choice and execute john. The result as shown below
john protected_key_john -wordlist=/usr/share/wordlists/rockyou.txt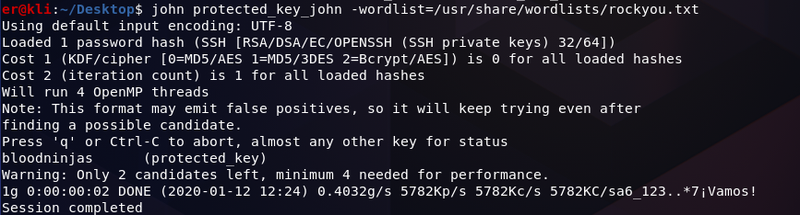
If the password in contained in the wordlist we used John will crack the key.
As you can see the process is very simple and easy. I hope this tutorial will help those who attempt to crack an ssh key for the first time!